A single breach can cripple payroll. In an incident reported on May 7, 2024, a major cyber-attack compromised a third-party payroll system used by the UK’s Ministry of Defence, exposing the names and bank details of approximately 270,000 service members. The attack highlighted the significant risks inherent in the software supply chain
IBM’s 2024 Cost of a Data Breach Report found that the average cost per record for stolen employee Personally Identifiable Information (PII) was $189. However, this figure is an average, and the true cost can vary dramatically based on industry and geography, with the overall average cost of a breach reaching $4.88 million globally.
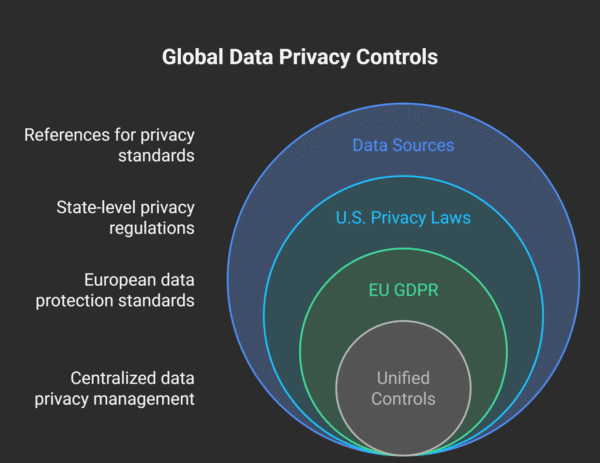
Payroll files pack salaries, Social Security numbers, tax IDs, and bank accounts—data the GDPR and California’s CPRA now guard with hefty fines for any lapse.
That’s why forward-looking HR and finance leaders are adopting payroll-data-protection software. This guide breaks down the seven security features that matter and the vendor questions that separate real safeguards from marketing fluff. Let’s protect every paycheck together.
The 2025 threat–and-compliance backdrop
Hackers have learned that the quickest way to hurt a company is to strangle payroll. Supply-chain attacks, exemplified by the 2023 MOVEit breach, demonstrate the cascading risk of a single vulnerability. A flaw in the widely used MOVEit file-transfer software was exploited by the Cl0p ransomware group, exposing the data of over 93 million individuals across more than 2,700 organizations, including the UK payroll provider Zellis. The incident, with estimated costs exceeding $10 billion, underscores that a company’s security is contingent on the integrity of its software suppliers. Even a well-guarded enterprise is only as strong as the file-transfer tool behind its pay run.
Regulators are raising the stakes. GDPR fines can reach €20 million or 4 % of global revenue, whichever is higher. California’s CPRA ended the long-standing HR-data exemption on January 1, 2023. This pivotal regulatory change extended the full suite of consumer privacy rights to California-based employees, applicants, and contractors. Consequently, these individuals now possess the right to know what personal information is collected about them, the right to request the deletion of their data, and the right to correct inaccurate information held by their employer. This expansion of rights creates significant new operational obligations for HR and payroll departments and mandates that payroll software platforms provide robust functionality to manage and fulfill these data subject requests. More than twenty U.S. states have now enacted their own privacy laws, creating a complex patchwork. Vanta’s GRC framework rolls the requirements of the five state laws already in force – CCPA/CPRA, CPA, CTDPA, UCPA and VCDPA – into a single control set and automates evidence collection, so payroll teams can get audit-ready faster.
Leadership feels the pressure. Industry analysis indicates a growing concern among HR and payroll leaders regarding data security, driven by increasing regulatory pressure and high-profile breaches. For example, a recent Sage report on South African businesses found that data security was a primary driver for cloud adoption, with 70% of respondents citing automated tax calculations and 56% citing centralized payroll and employee data as key benefits of cloud systems. When those worries collide with fines and brand damage, choosing secure payroll data protection software shifts from nice-to-have to non-negotiable.
With that context in place, let’s explore the seven capabilities that set truly secure payroll platforms apart.
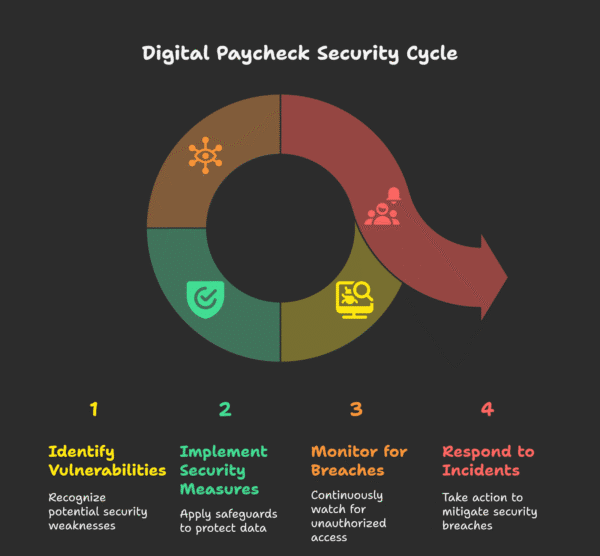
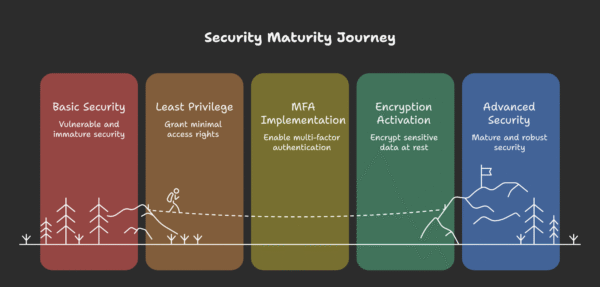
1. Lock down access with role-based permissions
Insider abuse is a significant threat. The Association of Certified Fraud Examiners (ACFE) 2024 Report to the Nations found that asset misappropriation, which includes payroll fraud, is the most common form of occupational fraud, occurring in 89% of cases. While these schemes have the lowest median loss at $120,000, the duration of fraud is a key factor; the typical fraud case lasts for a median of 12 months before detection. Furthermore, the perpetrator’s level of authority is strongly correlated with the size of the loss, with frauds committed by owners or executives resulting in a median loss of $500,000, compared to $60,000 for employees. The longer it stays hidden, the more salaries, Social Security numbers, and bank accounts an attacker or a disgruntled employee can siphon off.
The remedy is the principle of least privilege. Effective payroll-security software lets you define granular roles (payroll manager, HR assistant, finance reviewer) so each person sees exactly what they need and nothing more. A junior assistant might correct mailing addresses but never view net pay, while a finance reviewer can approve totals yet cannot alter bank details.
Strong platforms reinforce those walls with dual approval. Any attempt to change a routing number or add a new payee triggers a second-person sign-off and an indelible timestamp in the audit log. If something does go wrong, you can retrace every step and know precisely who touched what.
When you demo a solution, ask the rep to create a “limited HR temp” role on the spot. If the task takes more than a minute or they need to call engineering, move on. In 2025, tightly managed permissions are the baseline for serious payroll security.
2. Require multi-factor authentication every time
Passwords alone are brittle. The 2025 Verizon Data Breach Investigations Report (DBIR) confirms that stolen credentials remain a dominant initial access vector, implicated in 22% of confirmed breaches. When a single password is the only barrier to the payroll system, the entire organization’s financial integrity is at risk. Multi-factor authentication (MFA) is the essential control to mitigate this risk. However, it is crucial to recognize that not all MFA is created equal. Attackers are increasingly employing sophisticated techniques like Adversary-in-the-Middle (AiTM) phishing and session token hijacking to bypass weaker, phishable forms of MFA such as SMS codes and simple push notifications. Therefore, top-tier platforms must support and enforce modern, phishing-resistant authentication factors like FIDO2 security keys to provide meaningful protection. When one username and password unlock an entire payroll vault, every paycheck rests on the weakest link.
Multi-factor authentication (MFA) fixes that flaw. By adding a second proof—an authenticator-app code, a hardware key, or a fingerprint—you force criminals to steal two secrets at once. Even if a phisher tricks an employee out of a password, the break-in stalls at the second prompt. The extra step takes users seconds yet stops most credential-stuffing bots and social-engineering attempts.
Good payroll-security software makes MFA mandatory. Admins can flip a single switch that enforces it for everyone, from the CFO to a temporary HR intern. Top-tier platforms also support modern factors such as FIDO2 security keys (far stronger than SMS codes) and weave MFA into single sign-on so employees see one clean gateway while IT keeps control.
When you demo a system, ask two questions: Is MFA mandatory, or merely available? and how fast can we enable it for every account? If the answer involves plug-ins, work-arounds, or vague roadmap promises, keep shopping. A second factor should be first-class citizenship in any platform that protects paychecks.
3. Encrypt data in transit and at rest
Payroll information is currency in its purest form: account numbers, salaries, and tax IDs. Leaving it unencrypted is like setting a briefcase of cash on a park bench. Strong encryption shuts the locks, so even if thieves grab the briefcase, all they see is unreadable code.
Leading payroll-security platforms apply 256-bit AES encryption the moment a record hits disk and move every byte through a TLS 1.2 or higher tunnel. The keys live inside a dedicated hardware security module, safely outside the database. That single design choice matters: Strong encryption is a foundational control for data protection, mandated as an ‘appropriate technical measure’ under regulations like GDPR Article 32. While quantifying the exact ROI of encryption can be complex, its value is clear: it renders stolen data unreadable and useless to attackers. The absence of reasonable security controls like encryption can lead to significantly increased regulatory penalties in the event of a breach. Leading payroll platforms must apply strong, standardized encryption, such as 256-bit AES, to all data at rest and utilize secure transport protocols like TLS 1.2 or higher for all data in transit. Verification of these controls through SOC 2 reports or penetration test results is a critical due diligence step.
Regulators agree. GDPR Article 32 calls encryption an “appropriate technical measure,” and California’s CPRA increases penalties when “reasonable security” such as encryption is missing. If data leaks without encryption, fines multiply.
One overlooked gap is how payslips travel. If your provider still emails plain PDFs, insist on a secure self-service portal or, at minimum, password-protected files. During diligence, ask the vendor to provide evidence such as pen-test reports or SOC 2 controls that prove encryption is always on. If those documents do not appear quickly, move on; an open briefcase is never worth the risk.
4. Track everything with audit trails, then let real-time alerts do the shouting
The IBM Cost of a Data Breach 2024 report reveals that the average breach lifecycle is 258 days, comprising 194 days to identify the breach and an additional 64 days to contain it. This lengthy ‘dwell time’ before detection provides a critical window for attackers to operate unnoticed. Shortening this lifecycle has a direct and significant financial impact; breaches contained in under 200 days cost an average of $3.84 million, while those lasting longer cost $5.46 million—a difference of over $1.6 million. Comprehensive audit trails provide the necessary visibility, while modern, real-time alerting and anomaly detection are the mechanisms that shrink the detection window and trigger the rapid response needed to mitigate financial damage. Each login, salary change, or bulk export is time-stamped, user-stamped, and sealed against tampering. When regulators ask for proof of “appropriate accountability controls” under SOC 2 or GDPR Article 30, these logs speak for you. SOC 2 compliance software like Vanta automatically aggregates that evidence across your systems, so producing an audit-ready report can drop from weeks to hours.
Cameras alone do not stop crime; alarms do. Modern platforms layer real-time monitoring and AI-driven anomaly detection on top of the logs. If someone tries to download the full payroll at 2 a.m., the system pings you, suspends the session, and preserves forensic evidence in one motion. That instant reaction shortens the breach life cycle and, according to IBM, can save nearly $1 million in cleanup costs.
During a demo, filter the activity log for “salary change,” then set an alert for any export larger than last month’s total. If the rep cannot complete both steps in under two minutes, the platform is not ready to guard paychecks in 2025.
5. Demand rapid, automatic security updates
Unpatched software remains a primary gateway for attackers. The 2025 Verizon DBIR highlights a significant resurgence in this area, with the exploitation of vulnerabilities now serving as the initial access vector in 20% of all breaches—a 34% year-over-year increase. Events like the MOVEit attack, which stemmed from a single unpatched vulnerability in a file-transfer tool, prove that delayed patching can have catastrophic, supply-chain-wide consequences. Therefore, a vendor’s ability to deliver rapid, automatic security updates without requiring client action is not a convenience but a critical defense against a documented and growing threat vector. The 2023 MOVEit ransomware spree proved the point when payroll outsourcers that delayed a critical update saw millions of employee records posted on leak sites.
Cloud-native payroll data protection software closes those gaps in hours, not weeks. Engineers push fixes across every tenant the same day a vulnerability is disclosed, usually with no downtime and no action from your IT team. By morning, payroll clerks log in unaware that the system just avoided a costly incident.
When you vet a vendor, press for specifics:
- How long did you take to deploy your most recent critical patch?
- Do you publish release notes that flag security fixes?
- Is patching fully automatic, or must clients schedule maintenance windows?
A confident rep will answer in hours or days, not quarters or vague road maps. Anything slower leaves the door open for attackers.
6. Insist on airtight backups and disaster recovery
Payroll is a weekly heartbeat; miss one beat and the whole body panics. Payroll is a time-critical business function where any disruption has immediate consequences. While precise hourly downtime costs vary, the paramount importance of business continuity is clear. In the current threat landscape, a robust backup and disaster recovery (BCDR) strategy is not just about recovering from hardware failure; it is a cornerstone of ransomware resilience. The 2025 Verizon DBIR reports that ransomware was a component in 44% of all breaches. A strategy built on immutable, off-site backups with clearly defined and tested Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) is what enables an organization to recover its operations without capitulating to extortion demands. The fact that 64% of ransomware victims now refuse to pay the ransom is a testament to the growing effectiveness of such recovery capabilities. When that system is payroll, the indirect price tag includes angry staff, regulatory fines for late wages, and morale that takes months to repair.
Great payroll data protection software plans for the worst before it happens. Look for platforms that replicate data in near real time to a second region, shrinking your recovery-point objective to minutes. Just as vital is the recovery-time objective: leading vendors can spin up a fresh environment and resume pay runs within a few hours because they rehearse full failovers at least twice a year and share the results with customers.
Redundancy must extend beyond the primary cloud. Daily snapshots copied to immutable, off-site storage act as ransomware armor; if an attacker encrypts live data, a clean copy still waits in reserve under separate credentials.
During diligence, ask three blunt questions:
- What are your documented RPO and RTO for payroll data?
- Where are backups stored, and are they immutable?
- When was your last full-scale recovery test, and how long did it take?
Vendors who answer with precise numbers such as “RPO five minutes, RTO three hours, last test passed on February 8” earn a spot on your shortlist. Those who hedge with “We’ve never needed to” do not.
7. Verify certifications and the culture behind them
Security features live or die by the team that builds and operates them. Independent audits offer the fastest window into that culture. Independent, third-party attestations like SOC 2 and ISO 27001 are crucial proxies for a vendor’s security maturity. However, data from SaaS management platform Vertice reveals significant gaps in the software supply chain: based on its platform data, only 14% of SaaS vendors hold a current SOC 2 report, 10% are ISO 27001 certified, and just 8% have both. Alarmingly, the same report indicates that 19% of SaaS spending goes to vendors with no compliance certifications whatsoever. This attestation gap presents a major due diligence challenge. Furthermore, with the transition period for the updated ISO/IEC 27001:2022 standard ending on October 31, 2025, buyers must verify that vendors are certified against the current standard or have a clear transition plan. If a payroll provider cannot show a migration plan, the certificate could expire midway through your contract.If your organization operates from several offices, exploring an ISO 27001 multi-site certification can consolidate those audits and slash the total cost by roughly 40 percent.
Treat the conversation like a background check on your would-be partner in payroll data protection software:
- Ask for evidence. A recent SOC 2 Type II letter under NDA and an ISO 27001 certificate dated 2024 or later are table stakes.
- Trace the data trail. Where will EU employee records live, and can U.S. data stay onshore? GDPR fines escalate when residency promises break.
- Follow the chain. Which sub-processors handle tax filings or bank payouts, and do they carry the same certifications? The MOVEit supply-chain breach proved that one weak link can spill millions of pay records.
- Probe readiness. How fast will the vendor notify you of a breach? When did they last run a tabletop exercise? Practiced teams share playbooks; unprepared ones hide behind legalese.
A provider that answers every point with dated documents, clear diagrams, and visible SLAs signals a security culture you can audit and trust. One that dodges or defers invites you to become the next cautionary tale.
Frequently asked questions about payroll data protection
What is payroll data protection software?
It is a specialized platform that secures payroll files and processes through encryption, role-based access, audit logging, and other controls, ensuring employees are paid accurately while sensitive data stays private and compliant.
How does encryption protect payroll data?
Encryption converts readable information into cipher text that can only be unlocked with the proper keys. If attackers intercept or exfiltrate encrypted payroll files, the data remains unreadable and therefore useless to them.
Which certifications should a payroll security vendor have?
Look for an up-to-date SOC 2 Type II report and an ISO 27001:2022 certificate at a minimum. Additional attestations like ISO 27701 or FedRAMP can further demonstrate a mature security posture.
Wrapping it up
Payroll security is not a once-a-year audit; it is an everyday promise to the people who trust you with their most private details. We have walked through the seven capabilities that turn that promise into practice:
- Role-based, least-privilege access
- Mandatory multi-factor authentication
- End-to-end encryption in transit and at rest
- Always-on audit trails with real-time alerts
- Rapid, automatic security updates
- Tested backups and fast disaster recovery
- Third-party-verified security culture and certifications
Treat this list as your scorecard when you evaluate payroll data protection software. After each demo, ask: Did the vendor show every control working, and can they back each claim with fresh evidence? If the answer falls short of all seven, keep searching.
Security keeps evolving, so build for tomorrow as well as today. Pair your chosen platform with compliance tooling or SIEM integrations that watch for drift between audits. Invite your IT and security colleagues early; their questions will sharpen yours.
Choose wisely and you gain more than compliance. You add confidence that people will be paid on time, every time, regardless of tomorrow’s headlines. Your auditors move faster, your board sleeps easier, and your workforce sees a company that guards what matters most.
Print the checklist, keep it where you plan pay runs, and bring it to every meeting. Every paycheck, and every employee behind it, deserves the strongest lock you can buy.






Leave A Comment